Recent Phishing Attacks - In february 2024, change healthcare fell victim to an attack. The less information you post, the less data you make available to a cybercriminal for use in developing a potential attack or. The 5 biggest phishing attacks of 2024 1. The attacks use a specific phishing technique called “device code phishing” that tricks users to log into productivity apps while.
In february 2024, change healthcare fell victim to an attack. The 5 biggest phishing attacks of 2024 1. The attacks use a specific phishing technique called “device code phishing” that tricks users to log into productivity apps while. The less information you post, the less data you make available to a cybercriminal for use in developing a potential attack or.
The less information you post, the less data you make available to a cybercriminal for use in developing a potential attack or. The attacks use a specific phishing technique called “device code phishing” that tricks users to log into productivity apps while. The 5 biggest phishing attacks of 2024 1. In february 2024, change healthcare fell victim to an attack.
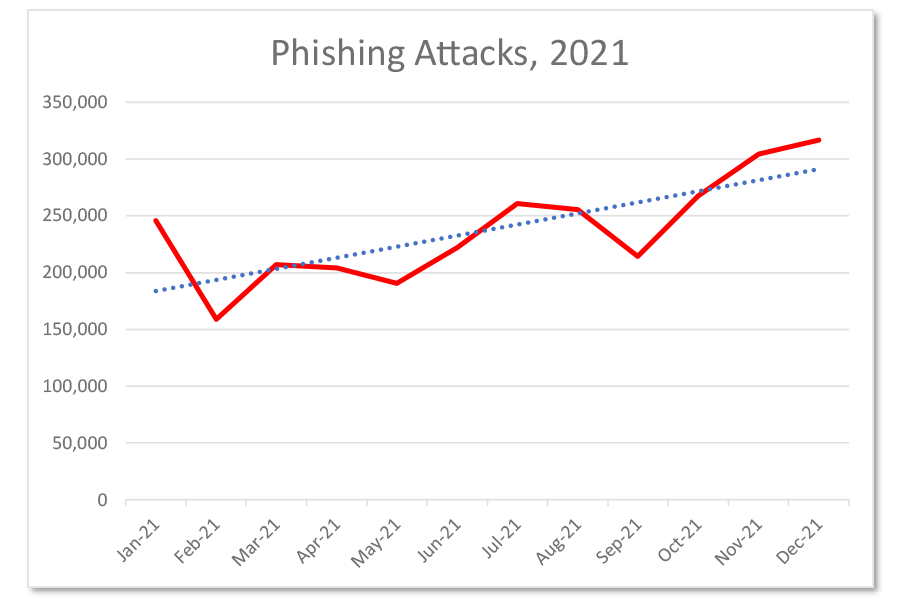
Global Phishing Attacks Reach New Heights in 2021 HelpDesk Baylor
In february 2024, change healthcare fell victim to an attack. The 5 biggest phishing attacks of 2024 1. The attacks use a specific phishing technique called “device code phishing” that tricks users to log into productivity apps while. The less information you post, the less data you make available to a cybercriminal for use in developing a potential attack or.
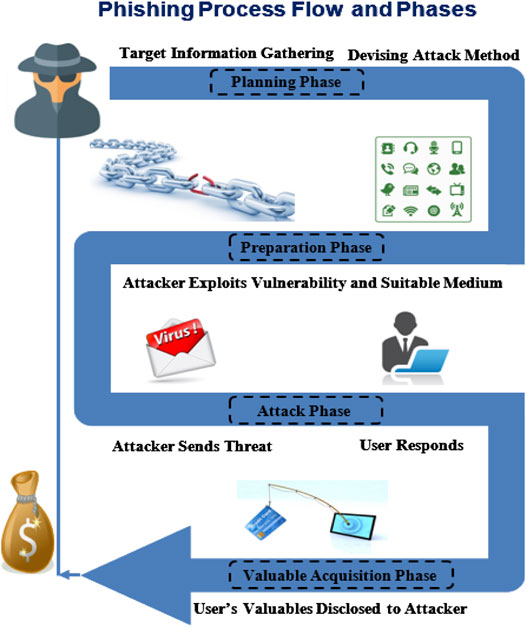
Frontiers Phishing Attacks A Recent Comprehensive Study and a New
In february 2024, change healthcare fell victim to an attack. The 5 biggest phishing attacks of 2024 1. The less information you post, the less data you make available to a cybercriminal for use in developing a potential attack or. The attacks use a specific phishing technique called “device code phishing” that tricks users to log into productivity apps while.
Be aware of most powerful phishing attack Egadgetportal
The attacks use a specific phishing technique called “device code phishing” that tricks users to log into productivity apps while. The less information you post, the less data you make available to a cybercriminal for use in developing a potential attack or. The 5 biggest phishing attacks of 2024 1. In february 2024, change healthcare fell victim to an attack.
20 types of phishing attacks + phishing examples Norton
The 5 biggest phishing attacks of 2024 1. In february 2024, change healthcare fell victim to an attack. The less information you post, the less data you make available to a cybercriminal for use in developing a potential attack or. The attacks use a specific phishing technique called “device code phishing” that tricks users to log into productivity apps while.
Novel Techniques Fueling Recent Rise in Phishing Attacks ChannelE2E
The attacks use a specific phishing technique called “device code phishing” that tricks users to log into productivity apps while. In february 2024, change healthcare fell victim to an attack. The 5 biggest phishing attacks of 2024 1. The less information you post, the less data you make available to a cybercriminal for use in developing a potential attack or.
6 Common Types of Cyber Attacks in 2021 and How To Prevent Them
The attacks use a specific phishing technique called “device code phishing” that tricks users to log into productivity apps while. In february 2024, change healthcare fell victim to an attack. The less information you post, the less data you make available to a cybercriminal for use in developing a potential attack or. The 5 biggest phishing attacks of 2024 1.
What is Phishing Attack? Types of Phishing & Recent Phishing Scam
The 5 biggest phishing attacks of 2024 1. The less information you post, the less data you make available to a cybercriminal for use in developing a potential attack or. In february 2024, change healthcare fell victim to an attack. The attacks use a specific phishing technique called “device code phishing” that tricks users to log into productivity apps while.
The 6 most common Phishing Attacks COMPTEC IT
The 5 biggest phishing attacks of 2024 1. The attacks use a specific phishing technique called “device code phishing” that tricks users to log into productivity apps while. In february 2024, change healthcare fell victim to an attack. The less information you post, the less data you make available to a cybercriminal for use in developing a potential attack or.
81 Phishing Attack Statistics 2025 The Ultimate Insight
The 5 biggest phishing attacks of 2024 1. The less information you post, the less data you make available to a cybercriminal for use in developing a potential attack or. The attacks use a specific phishing technique called “device code phishing” that tricks users to log into productivity apps while. In february 2024, change healthcare fell victim to an attack.
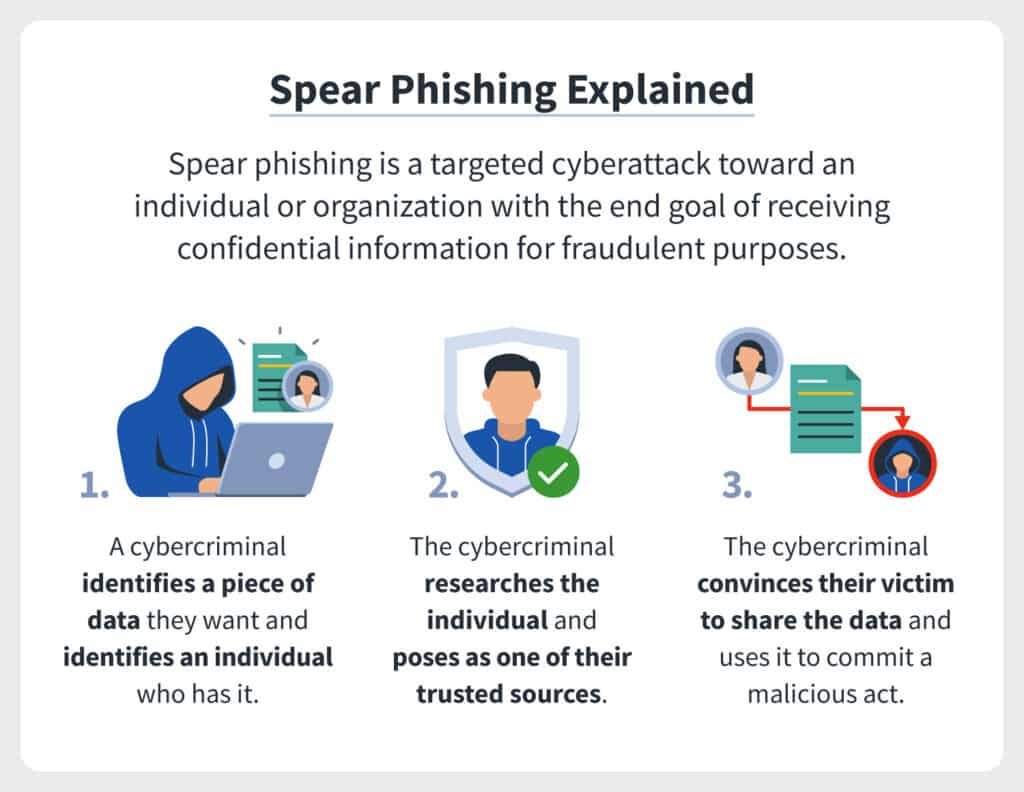
The Major Types of Phishing Attacks & How to Identify Definitive Guide
The 5 biggest phishing attacks of 2024 1. The less information you post, the less data you make available to a cybercriminal for use in developing a potential attack or. The attacks use a specific phishing technique called “device code phishing” that tricks users to log into productivity apps while. In february 2024, change healthcare fell victim to an attack.
The Attacks Use A Specific Phishing Technique Called “Device Code Phishing” That Tricks Users To Log Into Productivity Apps While.
The 5 biggest phishing attacks of 2024 1. The less information you post, the less data you make available to a cybercriminal for use in developing a potential attack or. In february 2024, change healthcare fell victim to an attack.