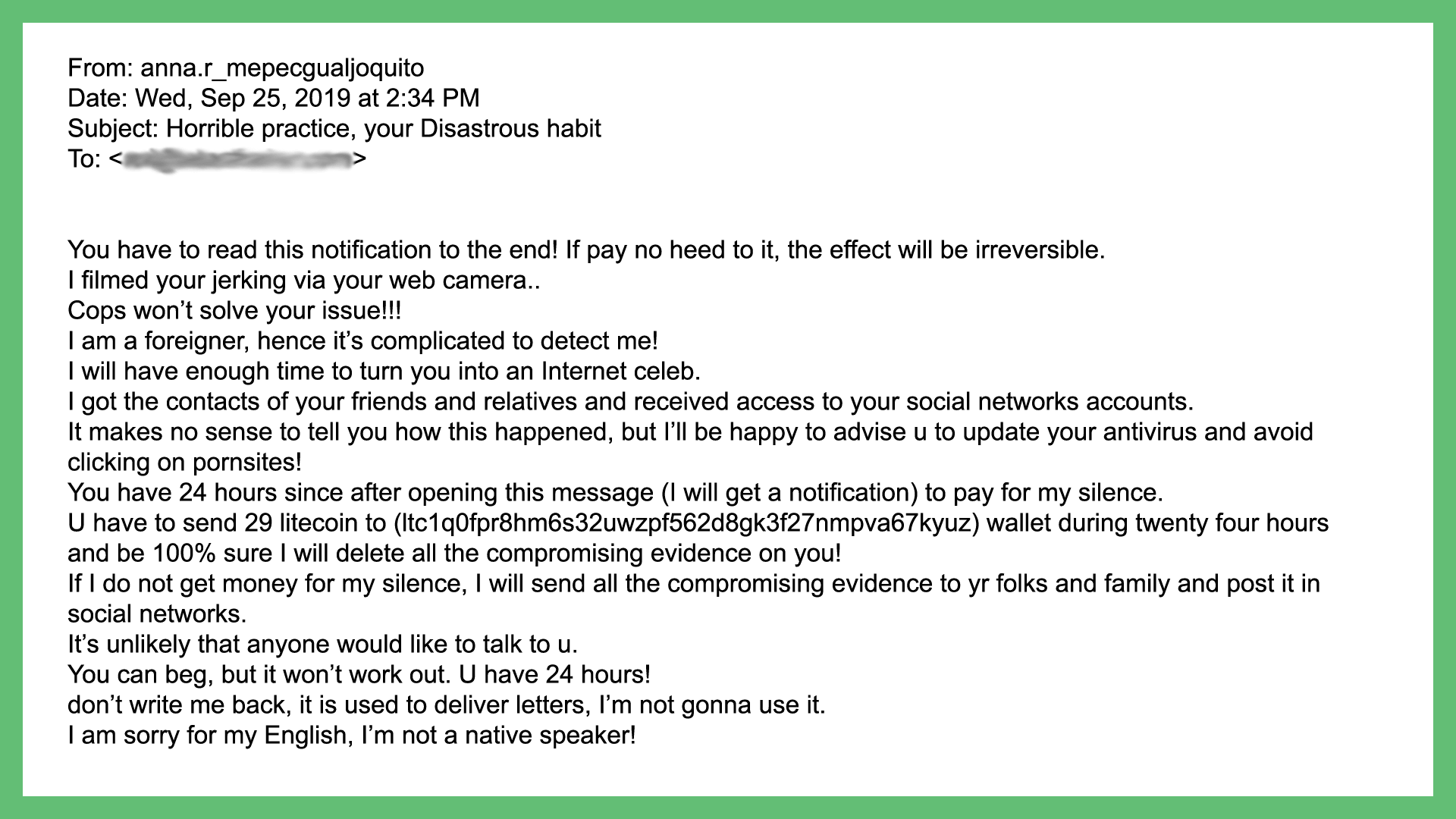
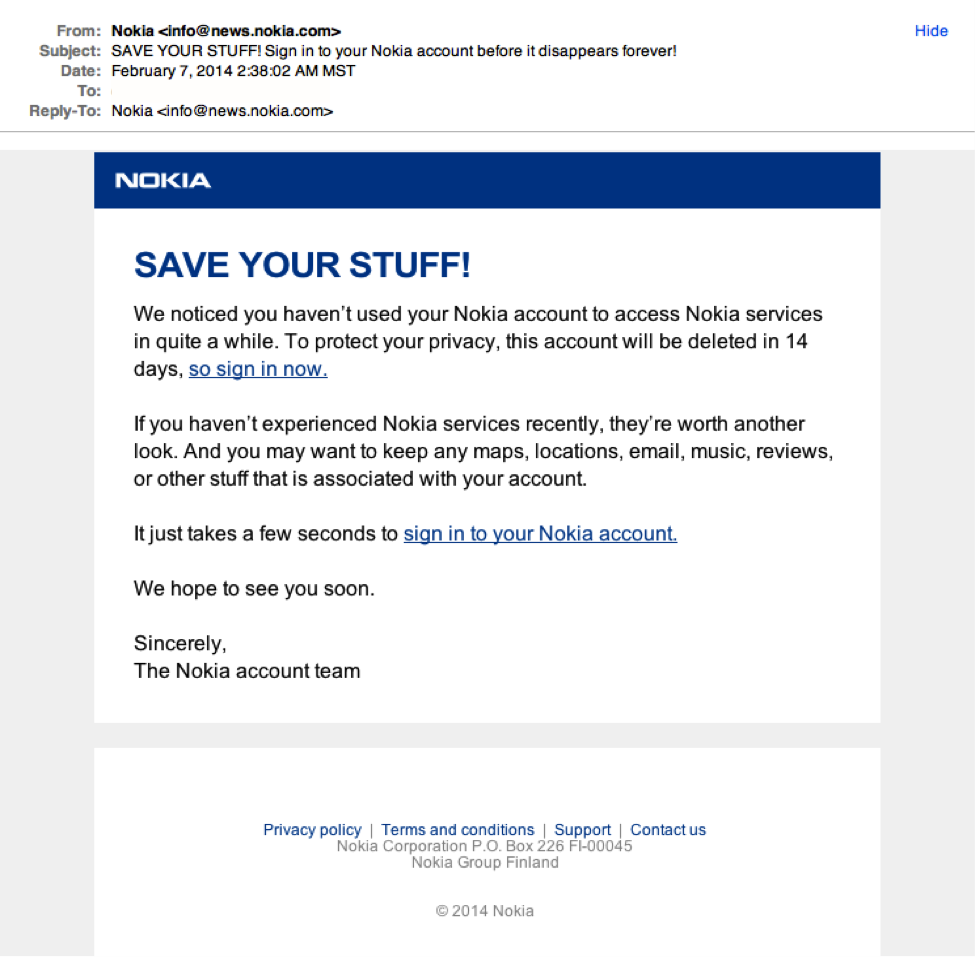
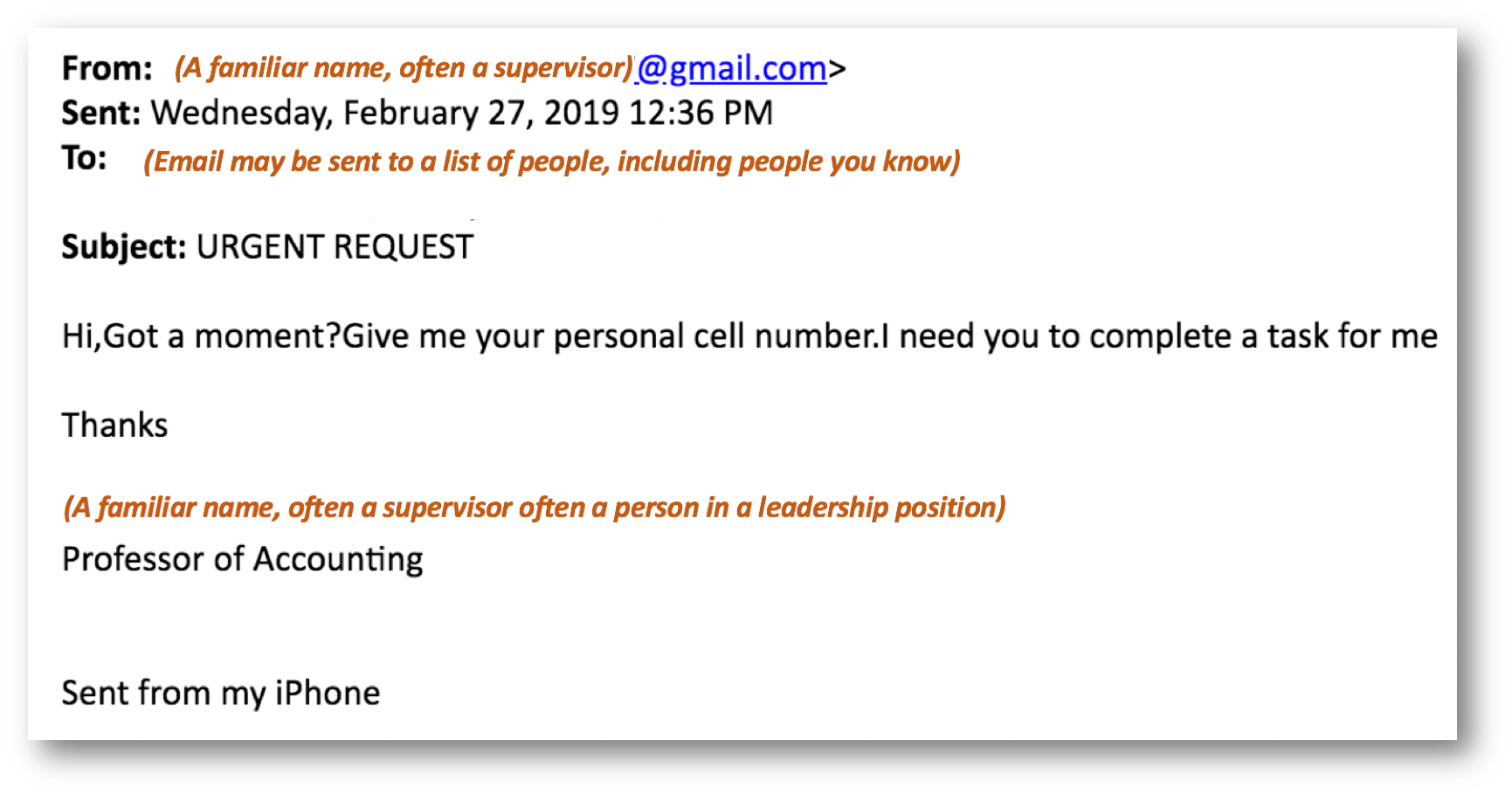
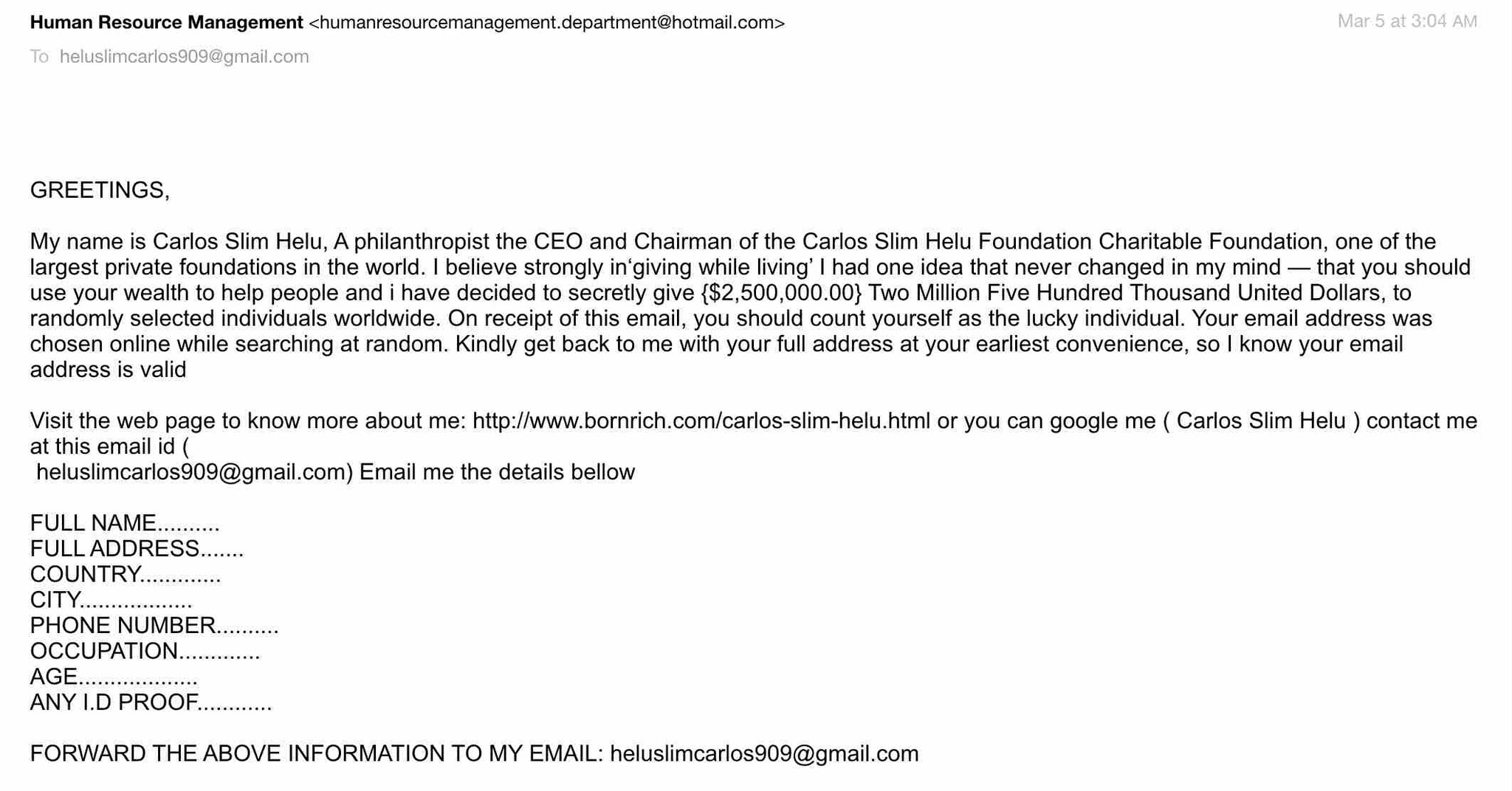
Scam Email Template - These types of emails provide employees with best practices for. Take an extra five minutes to verify something is legitimate. It takes less time than recovering.
Take an extra five minutes to verify something is legitimate. It takes less time than recovering. These types of emails provide employees with best practices for.
It takes less time than recovering. These types of emails provide employees with best practices for. Take an extra five minutes to verify something is legitimate.
Free Phishing Email Templates
It takes less time than recovering. These types of emails provide employees with best practices for. Take an extra five minutes to verify something is legitimate.
Free Phishing Email Templates
These types of emails provide employees with best practices for. Take an extra five minutes to verify something is legitimate. It takes less time than recovering.
7 Phishing Email Examples From Our Own Inbox — Etactics
Take an extra five minutes to verify something is legitimate. It takes less time than recovering. These types of emails provide employees with best practices for.
Fake Phishing Email Template
These types of emails provide employees with best practices for. It takes less time than recovering. Take an extra five minutes to verify something is legitimate.
Sample Phishing Email Templates
It takes less time than recovering. Take an extra five minutes to verify something is legitimate. These types of emails provide employees with best practices for.
Best Phishing Email Templates
Take an extra five minutes to verify something is legitimate. It takes less time than recovering. These types of emails provide employees with best practices for.
5 ways to detect phishing emails and scams
Take an extra five minutes to verify something is legitimate. It takes less time than recovering. These types of emails provide employees with best practices for.
Phishing Email Examples, Where to Report Email Scams? NOI
These types of emails provide employees with best practices for. It takes less time than recovering. Take an extra five minutes to verify something is legitimate.
Phishing Email Examples To Help You Identify Phishing Images
It takes less time than recovering. Take an extra five minutes to verify something is legitimate. These types of emails provide employees with best practices for.
It Takes Less Time Than Recovering.
Take an extra five minutes to verify something is legitimate. These types of emails provide employees with best practices for.